Security teams are constantly overwhelmed with hundreds to thousands of alerts being triggered daily. This often causes most alerts to be left unattended and real alerts to be overlooked. Investigating an alert is a laborious task that involves using tools and multiple data sources to collect and analyze forensic evidence which can take from weeks to months. Even when a real breach is detected, response is tedious, imprecise and can take days often requiring multiple tools and access to devices. With the use of an incident response platform alerts can be managed automatically, remediation can be performed remotely and the entire process can be reduced to just minutes.
Automatic Alert Investigation
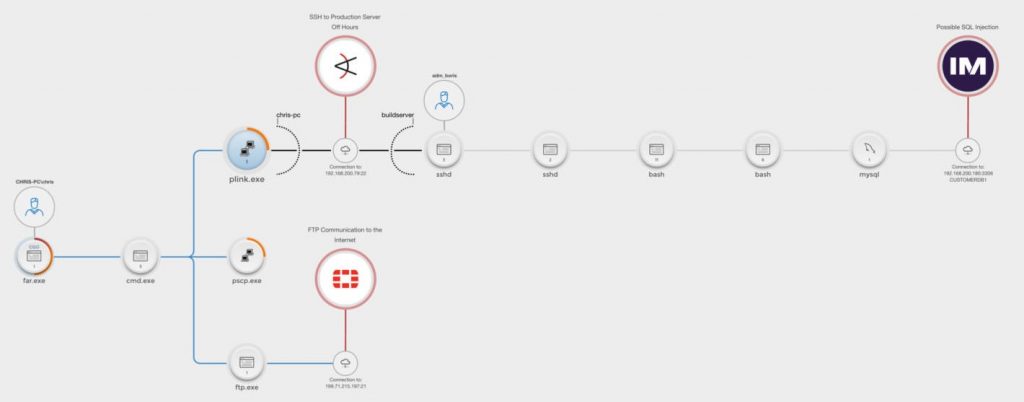
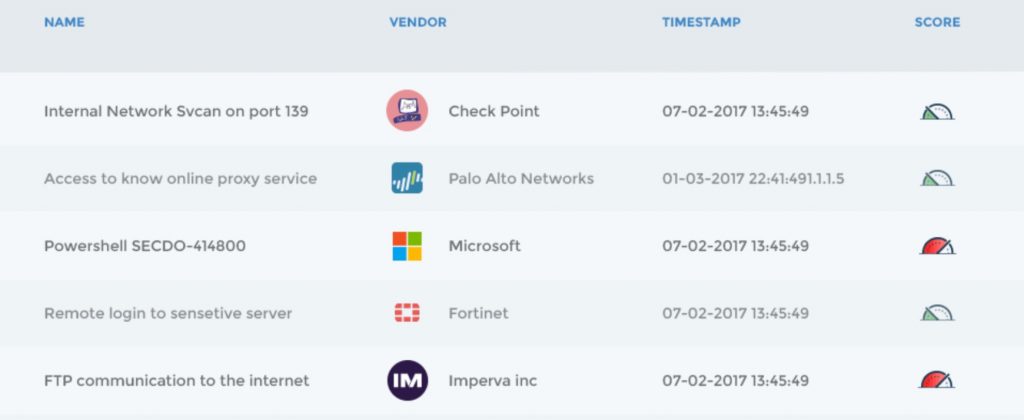
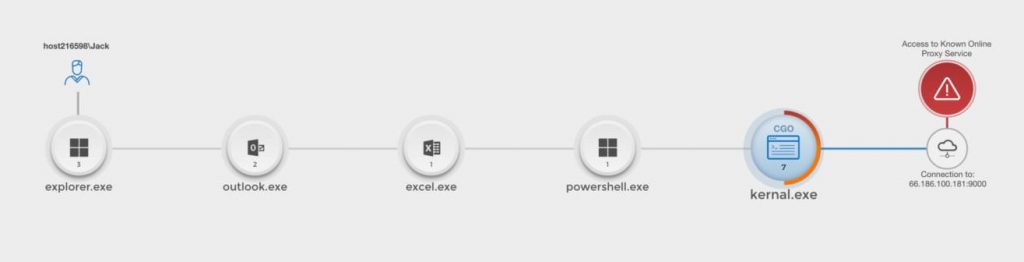
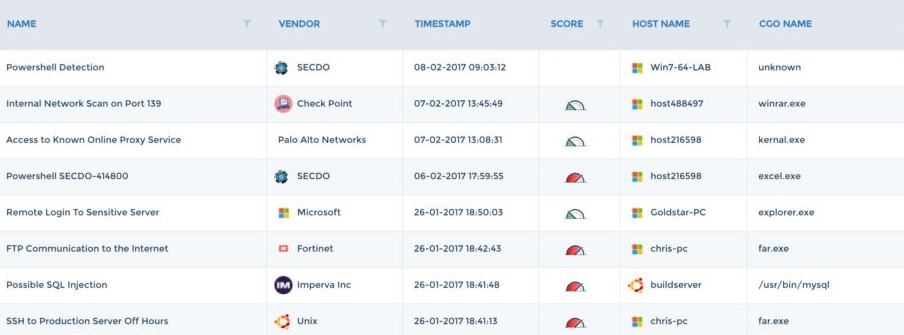
Know with quickness and certainty the details of any incident. Once an alert is received from a SIEM or any detection source, it becomes automatically correlated with the appropriate casualty chains. A complete context of the alert is then revealed, including a timeline of the attack chain back to the root cause, affected hosts, involved entities, and a full damage assessment.
Continuous endpoint and Server Data Collection
All events and behaviors are continuously recorded on every host and stored on either an on-premise or cloud server. They are retained for years with recorded activities including: Network, Registry, File, Process, Event Log, User, and USB.
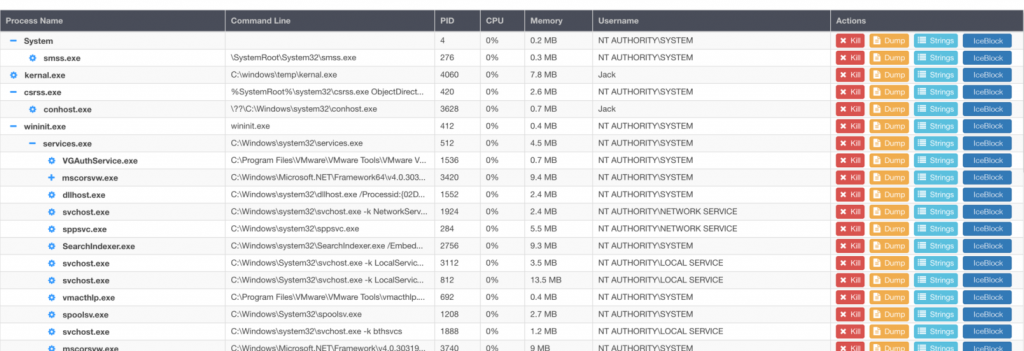
Remediation and Real-Time Response
Obtain powerful, remediation and granular response tools. IT and security teams can remotely view, assess, retrieve, isolate, contain and delete individual processes on any host. Users may also continue to work while the investigation is underway with no interruption in activity and no downtime.
Some of the main benefits of having an incident response solution:
Slash incident response time to minutes Minimize the damage and disruption of a breach Access breach damage accurately and immediately Increase the productivity of security teams Gain complete visibility into all hosts.